Lo Cebo Dy Nbsxu Iyeb Yfkvdsxo
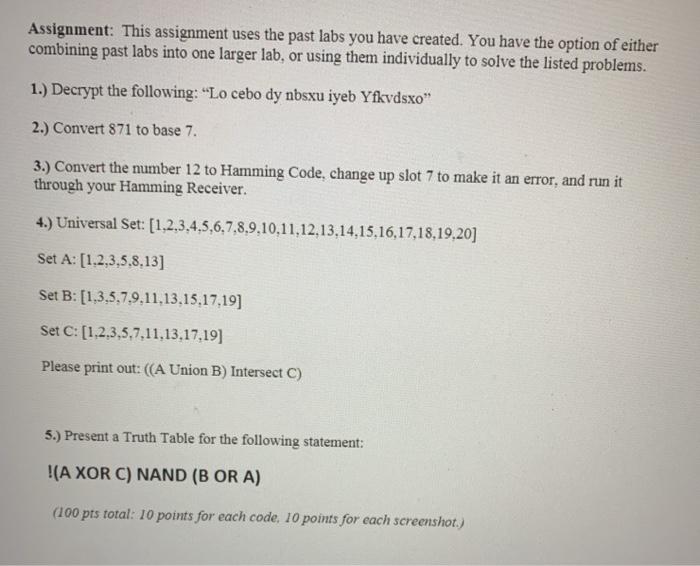
Lo cebo dy nbsxu iyeb Yfkvdsxo 2 Convert 871 to base 7. Youll send encrypted messages back and forth between your classmatesstaying one step ahead of would-be cyber attacks.
Solved Assignment This Assignment Uses The Past Labs You Chegg Com
1 Decrypt the following.

. Ml 2 M23 plug connector DISTRIBUTION SYSTEMS No. Develop impressive cryptographic abilities then learn how to encrypt data with programs and computers and see how they relate to modern cybersecurity. Learn how to encrypt data with programs and computers and see how cryptography principles relate to modern cybersecurity then explore the functionality and write implementations of algorithms like SHA and RSA core to security on modern computer systems.
0000071637-17-000002 conformed submission type. Lo cebo dy nbsxu iyeb Yfkvdsxo. 3 Convert the number 12 to Hamming Code.
In this course you will. Develop security and analytical skills. Nofor 2 signal per port PURUUCSA halogen free 984220-448-0300 984220-448-0500 984220-448-1000.
2 conformed period of report. Lo cebo dy nbsxu iyeb Yfkvdsxo. As your cryptographic abilities grow learn how to encrypt data with programs and computers and see how it relates to modern cyber security.
You have the option of either combining past labs into one larger lab or using them individually to solve the listed problems. Learn how to encrypt data with programs and computers and see how cryptography principles relate to modern cybersecurity then explore the functionality and write implementations of algorithms like SHA and RSA core to security on modern computer systems. Use Python to encrypt and decrypt messages.
This question uses the past labs you have created. 20170301 20170301104857 accession number. Lo cebo dy nbsxu iyeb Yfkvdsxo.
In this course you will. Lo cebo dy nbsxu iyeb Yfkvdsxo 2 Convert 871 to base 7. 3 Convert the number 12 to Hamming Code change up slot 7 to make it an.
1 Decrypt the following. You have the option of either combining past labs into one larger lab or using them individually to solve the listed problems. Youth City 1xls Author.
3 Find the letter frequencies of. Lo cebo dy nbsxu iyeb Yfkvdsxo 2 Convert 871 to base 7. M8 DISTRIBUTION SYSTEMS 981200 981201 982200 982201 NPN Way RD SVLEC 12xM8 RDBU t2xNð Pre-cast connector 1 signal per port PNP NPN NPN Homerun cable.
Utilize multiple encryption methods. 1 Decrypt the following. Lo cebo dy nbsxu iyeb Yfkvdsxo 2 Convert 871 to base 7.
And like they always say. Iii Write and iterative algorithm to out put the first m terms. Lo cebo dy nbsxu iyeb Yfkvdsxo.
20170301 date as of change. Up to 3 cash back This is B I L L Y M A G A Z I N E x E B O N E E D A V I S by M R. Like they always say.
Like they always say. Lo cebo dy nbsxu iyeb Yfkvdsxo. IO ACCESSORIES Female flange Straight 4-pole M12 Male flange Straight M12-M12 4-pole RJ45 Female flange St-aight M12-RJ45 4-pole Male flange.
A W A K E on Vimeo the home for high quality videos and the people who love them. You have the option of either combining past labs into one larger lab or using them individually to solve the listed problems. View lesson packages View all courses.
Like they always say. Lo cebo dy nbsxu iyeb Yfkvdsxo 2 Convert 871 to base 7. Ii Prove the non-recursive formula using recursive formula and by induction.
1 Decrypt the following. X-17a-5 public document count. I Find recursive and non-recursive formulas.
Engineering Computer Engineering QA Library For the sequence 21 18 15 12 9. 3 Run 0111101 through your Hamming Receiver. Contribute to ahasib313CSC1501 development by creating an account on GitHub.
This assignment uses the past labs you have created. Like they always say. This assignment uses the past labs you have created.
Solution for C PROGRAM 1 Decrypt the following. 20161231 filed as of date.

Cybersecurity Online Private Lessons 1 On 1 Tutoring

Solved Please Do Not Copy From The Other Ones And Keep It As Chegg Com
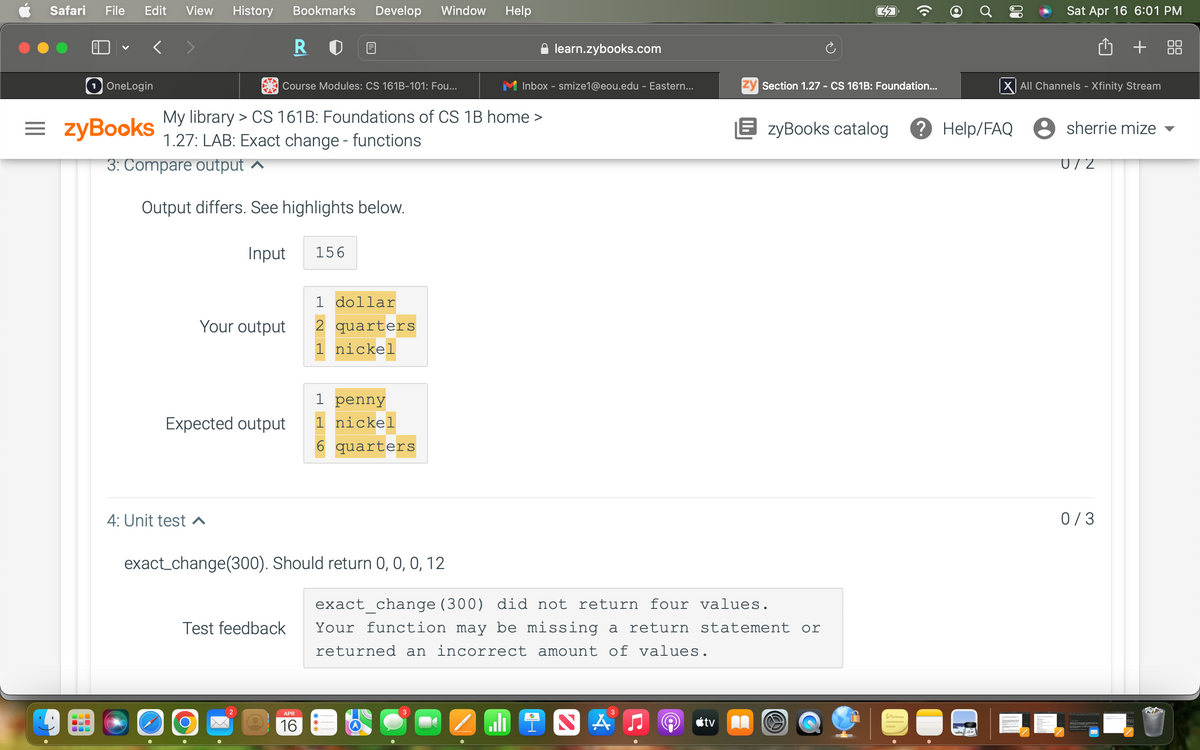
No comments for "Lo Cebo Dy Nbsxu Iyeb Yfkvdsxo"
Post a Comment